VLAN Access Lists (VACLs)
VACLs are another good layer of security to help control who can talk to who, much like access control lists that are in firewalls and routers, however the difference is VACLs operate at layer two of the OSI model. There could be situations where you have multiple hosts on the same LAN and want to block traffic from reaching certain hosts within that same network, how would you go about blocking that type of traffic without using a router or firewall? (Hint: Create a VACL)
In this post we have a DMZ and an INTERNAL network. The goal is to block DMZ systems from reaching other servers in the DMZ. We have are standard "out of the box" configuration firewall that is between the DMZ and INTERNAL network. In this example the firewall is configured with security-levels in place. The INTERNAL zone has a security-level of 100 and the DMZ zone as a security-level 80. We have two VLANs on this switch, VLAN two (2) which is the DMZ and VLAN three (3) which is the INTERNAL VLAN. The firewall is using the "router on a stick" configuration and trunking VLANs on the single interface, and we have four servers total. Two DMZ servers and two INTERNAL servers are in this example.
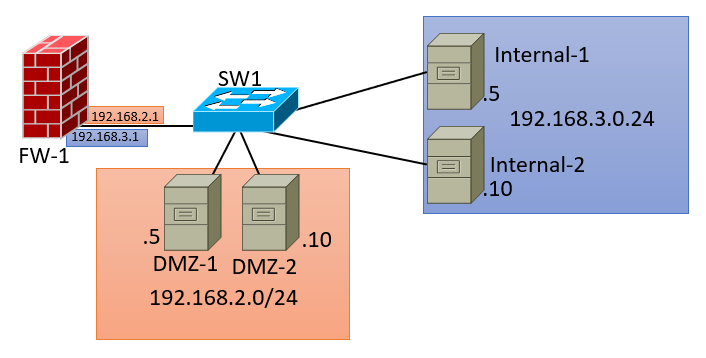
The INTERNAL servers can reach the DMZ servers, however the DMZ servers can't reach the INTERNAL systems which is expected because of the security-levels that are configured on the firewall. However the DMZ servers can reach other, to disable that we need to create an ACL on the switch before we create a VACL :)
1ip access-list extended BLK-DMZ-COMS permit ip 192.168.2.0 0.0.0.255 192.168.2.0 0.0.0.255
This extended ACL is used to identify the source and destination traffic that we want to block. In this example this ACL matches DMZ servers talking to other DMZ servers in the 192.168.2.0/24 network. Next we have to build a VLAN access map, in this example I'm calling it "VACL-BLK-DMZ-COMS".
1vlan access-map VACL-BLK-DMZ-COMS 10 match ip address BLK-DMZ-COMS action drop
This VLAN access map matches the IP address in our ACL that we created as well as the action to take if a match is successful. However just like ACLs VLANs access-maps have an implicit deny so we need to add another entry to the access map to allow everything else.
1vlan access-map VACL-BLK-DMZ-COMS 20 action forward
The final thing is to apply this VACL that we just created to the VLAN we want this VACL to apply enforce, which would be VLAN 2.
1vlan filter VACL-BLK-DMZ-COMS vlan-list 2
That's it! We have just enabled this VACL onto VLAN 2, the DMZ servers can no longer talk to each other. Our internal systems can still reach both of the DMZ systems just like we wanted. I hope this information is helpful,
If you are using Cisco VIRL here is a link on GitHub to the file I was working with.