ASA Site to Site VPN (DHCP)
If you don’t already know, site to site VPNs can be a cost-effective way for remote sites to connect to HQ resources instead of a lease line like using MPLS or Metro-E circuits. We can instead use a standard internet connection with a static IP, this is usually cheaper than a dedicated circuit. Our next steps are purchasing a firewall for the remote site (assuming you already have one at HQ) and setup a site to site VPN connection to make the connection. In this guide, I’ll demo a site to site VPN with a pair of ASAs as well as some additional commands to allow DHCP across the tunnel so that your HQ DHCP server can hand out addresses instead of configuring a local DHCP server at the remote site.
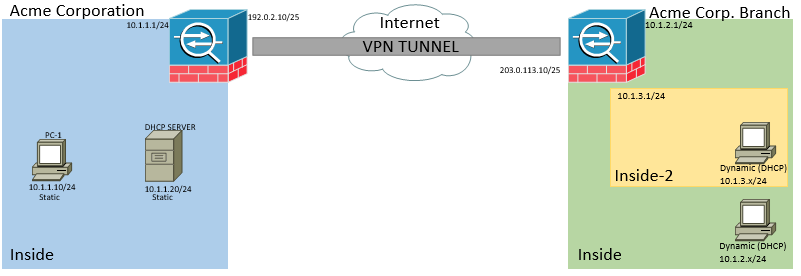
The table below goes over the agreed settings and what networks are protected. Also note that the “public” IP addresses listed in this example are from RFC 5737 and are not publicly available. Since this is a VPN connection we must agree on some common settings before traffic is allowed across it. We will be tunneling the entire address range for both sites and no need to NAT anything because its Acme’s network. Reference the table below:
| Acme Corp | Acme Branch |
|---|---|
| Peer IP Address: 192.0.2.10 | Peer IP Address: 203.0.113.10 |
| Phase 1: AES 256 SHA (Group 2) | Phase 1: AES 256 SHA (Group 2) |
| Phase 2: AES 128 SHA | Phase 2: AES 128 SHA |
| PFS: No | PFS: No |
| Protected Networks: 10.1.1.0/24 | Protected Networks: 10.1.2.0/24 |
| Preshared Key: cisco | Preshared Key: cisco |
Here is the topology below for reference:
Let's start building the tunnel on the Acme Corp side first by creating object groups:
1object network VPN-REMOTE-ACME-BRANCH-NET-1
2 subnet 10.1.2.0 255.255.255.0
3object network VPN-REMOTE-ACME-BRANCH-NET-2
4 subnet 10.1.3.0 255.255.255.0
5object network ACME-CORP-NET
6 subnet 10.1.1.0 255.255.255.0
7object network VPN-REMOTE-ACORP-BRANCH-NET-1
8 subnet 10.1.2.0 255.255.255.0
9object network VPN-REMOTE-ACORP-BRANCH-NET-2
10 subnet 10.1.3.0 255.255.255.0
11object-group network VPN-LOCAL-ACMECORP-NET
12 network-object object ACME-CORP-NET
13object-group network VPN-LOCAL-ACORP
14 network-object object ACME-CORP-NET
15object-group network VPN-REMOTE-ACORP-BRANCH
16 network-object object VPN-REMOTE-ACORP-BRANCH-NET-1
17 network-object object VPN-REMOTE-ACORP-BRANCH-NET-2
Next we need to create an access control list to match the traffic we want protected over the tunnel.
1access-list ACL-VPN-ACORP-ACORP-BRANCH extended permit ip object-group VPN-LOCAL-ACORP object-group VPN-REMOTE-ACORP-BRANCH
We have to create some NAT exemption rules as we don't want to NAT these networks when we are crossing over the VPN. On line one (1) I’m creating a single static NAT entry to reference Acme's Branch networks going to Acme's local networks.In line two (2) just reversing so that Acme's local network can reach Acme's Branch.
Notice: I'm not changing the source or destination address for these NAT rules.
1nat (Outside,Inside) source static VPN-REMOTE-ACORP-BRANCH VPN-REMOTE-ACORP-BRANCH destination static VPN-LOCAL-ACORP VPN-LOCAL-ACORP no-proxy-arp
2nat (Inside,Outside) source static VPN-LOCAL-ACMECORP-NET VPN-LOCAL-ACMECORP-NET destination static VPN-REMOTE-ACORP-BRANCH VPN-REMOTE-ACORP-BRANCH no-proxy-arp
Create a VPN Group Policy for Acme and Acme's Branch VPN connection
1group-policy GP-VPN-ACORP-ACORP-BRANCH internal
2group-policy GP-VPN-ACORP-ACORP-BRANCH attributes
3 vpn-tunnel-protocol ikev1
Create the tunnel
1tunnel-group 203.0.113.10 type ipsec-l2l
2tunnel-group 203.0.113.10 general-attributes
3 default-group-policy GP-VPN-ACORP-ACORP-BRANCH
4tunnel-group 203.0.113.10 ipsec-attributes
5 ikev1 pre-shared-key cisco
6 isakmp keepalive disable
Build the cryptomap:
1crypto map CM-ACORP-ACORP-BRANCH 1 match address ACL-VPN-ACORP-ACORP-BRANCH
2crypto map CM-ACORP-ACORP-BRANCH 1 set peer 203.0.113.10
3crypto map CM-ACORP-ACORP-BRANCH 1 set ikev1 transform-set ESP-AES-128-SHA
4crypto map CM-ACORP-ACORP-BRANCH interface Outside
Let's jump to Acme's Branch ASA and configure it to get this tunnel up. Let's create some object-groups.
1object network ACME-BRANCH-NET-1
2 subnet 10.1.2.0 255.255.255.0
3object network ACME-BRANCH-NET-2
4 subnet 10.1.3.0 255.255.255.0
5object network VPN-REMOTE-ACME
6 subnet 10.1.1.0 255.255.255.0
7object-group network VPN-LOCAL-ACME-BRANCH
8 network-object object ACME-BRANCH-NET-1
9 network-object object ACME-BRANCH-NET-2
10object-group network VPN-REMOTE-ACORP
11 network-object object VPN-REMOTE-ACME
Create the access control list to match the traffic we want protected on Acme's branch.
1access-list ACL-VPN-ACORP-BRANCH-ACORP extended permit ip object-group VPN-LOCAL-ACME-BRANCH object-group VPN-REMOTE-ACORP
Just like before we have to create some NAT exemption rules, Acme's Branch has two networks that need to go over the tunnel so we'll add them here. Line one (1) and two (2) is one network of Acme's Branch. Line three (3) and four (4) is another network that Acme's Branch has and with these two networks we are allowing both an inbound and outbound connection from the VPN.
1nat (Inside,Outside) source static ACME-BRANCH-NET-1 ACME-BRANCH-NET-1 destination static VPN-REMOTE-ACORP VPN-REMOTE-ACORP no-proxy-arp
2nat (Outside,Inside) source static VPN-REMOTE-ACORP VPN-REMOTE-ACORP destination static ACME-BRANCH-NET-1 ACME-BRANCH-NET-1 no-proxy-arp
3nat (Outside,Inside-2) source static VPN-REMOTE-ACORP VPN-REMOTE-ACORP destination static ACME-BRANCH-NET-2 ACME-BRANCH-NET-2 no-proxy-arp
4nat (Inside-2,Outside) source static ACME-BRANCH-NET-2 ACME-BRANCH-NET-2 destination static VPN-REMOTE-ACORP VPN-REMOTE-ACORP no-proxy-arp
Create a VPN Group Policy for Acme's Branch and Acme Corp VPN connection:
1group-policy GP-VPN-ACORP-BRANCH-ACORP internal
2group-policy GP-VPN-ACORP-BRANCH-ACORP attributes
3 vpn-tunnel-protocol ikev1
Create the tunnel:
1tunnel-group 192.0.2.10 type ipsec-l2l
2tunnel-group 192.0.2.10 general-attributes
3 default-group-policy GP-VPN-ACORP-BRANCH-ACORP
4tunnel-group 192.0.2.10 ipsec-attributes
5 ikev1 pre-shared-key cisco
6 isakmp keepalive disable
Build the cryptomap:
1crypto map CM-ACORP-BRANCH-ACORP 1 match address ACL-VPN-ACORP-BRANCH-ACORP
2crypto map CM-ACORP-BRANCH-ACORP 1 set peer 192.0.2.10
3crypto map CM-ACORP-BRANCH-ACORP 1 set ikev1 transform-set ESP-AES-128-SHA
4crypto map CM-ACORP-BRANCH-ACORP interface Outside
We now have configured everything for the tunnel to come up but we are missing DHCP, in this example since I don't have Windows DHCP server available I have configured an IOS router to do DHCP, which is on the Acme Corp network (10.1.1.20). To make DHCP available over the tunnel we only have to focus on Acme's Branch ASA and add in the following configuration:
1dhcprelay server 10.1.1.20 Outside
2dhcprelay enable Inside
3dhcprelay enable Inside-2
4dhcprelay timeout 60
We should be able to get an IP adderess from Acme's DHCP server, if I jump over to one of the Windows hosts on the Acme Branch and issue ipconfig /all we can see that this windows host was able to reach the DHCP server 10.1.1.20 which is over the VPN:
1C:\Documents and Settings\VIRL>ipconfig /all
2Windows IP Configuration
3
4 Host Name . . . . . . . . . . . . : VIRL-D3D4EE00AA
5 Primary Dns Suffix . . . . . . . :
6 Node Type . . . . . . . . . . . . : Unknown
7 IP Routing Enabled. . . . . . . . : No
8 WINS Proxy Enabled. . . . . . . . : No
9
10Ethernet adapter Local Area Connection:
11
12 Connection-specific DNS Suffix . :
13 Description . . . . . . . . . . . : Red Hat VirtIO Ethernet Adapter
14 Physical Address. . . . . . . . . : FA-16-3E-59-67-A3
15 Dhcp Enabled. . . . . . . . . . . : Yes
16 Autoconfiguration Enabled . . . . : Yes
17 IP Address. . . . . . . . . . . . : 10.1.2.61
18 Subnet Mask . . . . . . . . . . . : 255.255.255.0
19 Default Gateway . . . . . . . . . : 10.1.2.1
20 DHCP Server . . . . . . . . . . . : 10.1.1.20
21 Lease Obtained. . . . . . . . . . : Sunday, April 09, 2017 5:29:25 PM
22 Lease Expires . . . . . . . . . . : Monday, April 10, 2017 5:29:25 PM
23
24C:\Documents and Settings\VIRL>
If you want to try this out I have attached the running-configs of both firewalls at the end of this post. If you are using Cisco VIRL here is a link on GitHub to the file I was working with.
Note: When working with this file I noticed sometimes that the network switches on both sides don't always hold a MAC address table when we first start them. The workaround I found is you just copy the configuration delete the switch and add it back and plug everything back in order.
There is a subtype that is added in this configuration which was the Windows XP image I was working with. You can find more information about import Windows VMs and other 3rd Party systems into VIRL by checking out a previous post: Cisco VIRL and Windows VMs
As always I hope this is helpful! :)