RBAC Radius with Microsoft NPS 2012 R2
In this configuration I'm at looking at using Microsoft NPS 2012 R2 as radius server and I’m going to skip the installation of NPS because it really is just a next, next, finish installation. In this demo I already have this NPS system connected to a Windows domain, my goal is to create role based access on Cisco IOS routers while using radius to login. I’ll have a couple for active directory accounts each them will represent different types of allowed access to these IOS routers. One account will get full administrative access while the other will only get read access, how cool cat is that ;)
We have to get some house-cleaning things done first before we jump into it. To keep this simple in this example I'm only using one router and this router is able to reach the radius server. I’ll have to create an enable secret on the device, create a local username with a password, and turn AAA (Authentication, Authorization, Accounting). I like to create my own AAA method lists one for the console logins and one for remote logins here is what I got so far:
1enable secret 0 cisco
2username admin privilege 15 secret 0 cisco
3aaa new-model
4aaa authentication login OPEN-CONSOLE none
5aaa authentication login RADIUS-LOCAL group radius local-case
6aaa authorization exec default group radius if-authenticated
The router needs to know where radius server is located, we also need to put in a radius key and this needs to match between both the router and radius server.
1radius server RADIUS
2address ipv4 192.168.5.10 auth-port 1812 acct-port 1813
3key cisco123
If our router has more than one active interface we also should specify which IP interface we want the radius information to come from. In this example GigabitEthernet 0/1 will be the source interface.
1ip radius source-interface GigabitEthernet0/1
Apply this AAA method to the console and VTY ports:
1line con 0 login authentication OPEN-CONSOLE exit
2line vty 0 4 login authentication RADIUS-LOCAL
The magic begins with the Microsoft NPS server although any radius server is just as magical. We first have to create our client list within the Microsoft NPS. I have just used the defaults and have kept note of the radius key we configured earlier. This is pretty simple, expand the Radius Clients and Servers folder and right-click on Radius Clients and select new.
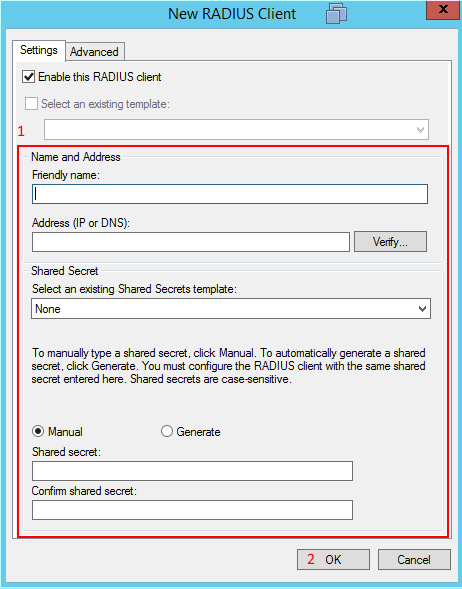
A new window will show, populate the information with a friendly name of the device you wish to add, IP address of the device and the radius key. After that select OK.
NOTE: Make sure the address matches to what you have configured as the source-interface on the router in this example it was GigabitEthernet0/1.
Once we have the all the clients in the client list we can now go to the Connection Request Polices. I usually just delete the existing policy, Use Windows authentication for all users and create a new policy called Radius-Login. Right-click on the Connection Request Policy folder, select new and follow these steps:
- Add a policy name and click next.
- Add a condition, (I usually do a a day and time condition and select the time frame you want logins to occur. Select next.
- Accept the defaults, Authenticate requests on this server, select next.
- Don't override anything, select next
- Leave the defaults which is blank on everything, select next.
- At the Connection Request Policy summary page it should look like something like below, select finish.
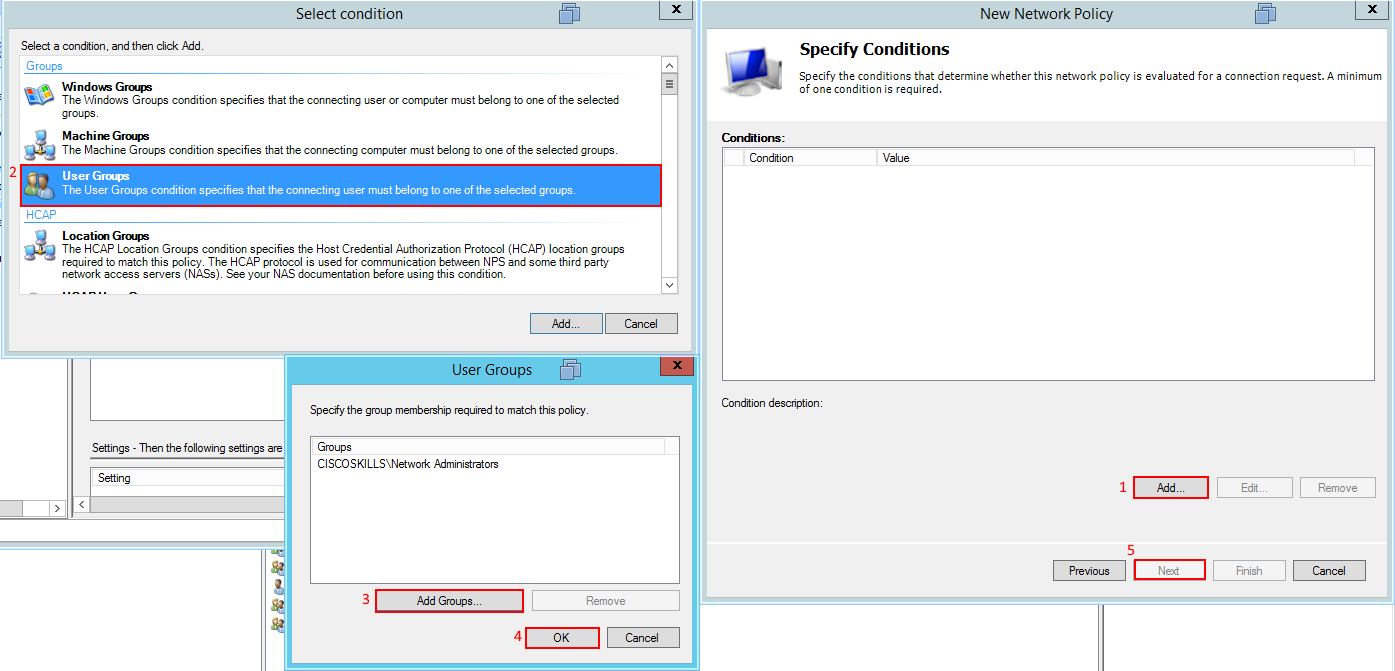
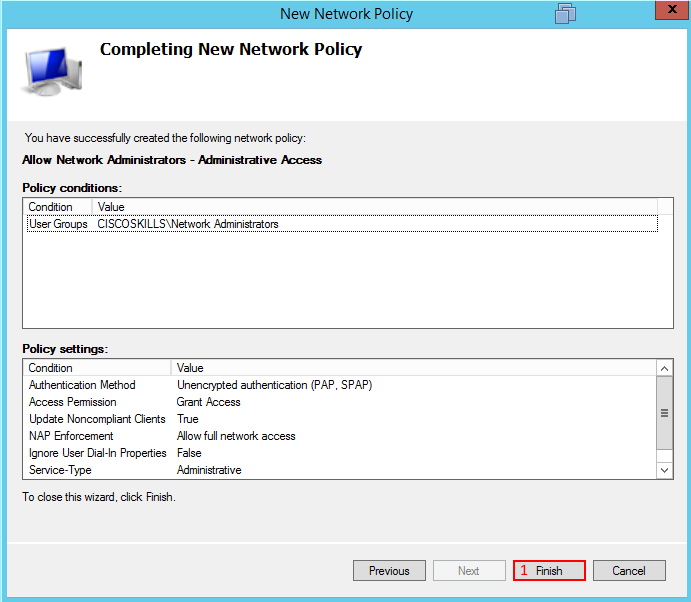
Go to the Network Policy Folder you will see some policies already created, delete those policies. We are going to create our own and the first policy is going to be a Network Administrators policy which will give full access to the IOS router if the user belongs to the correct Windows Security group. Right-click on the Network Policy folder and select new, new window will appear. Type in the policy name. In this example I'm using Allow Network Administrators - Administrative Access, select next. Under conditions select User Groups and in this example I have already created a security group on the Windows directory called Network Administrators, select next. On the following screen grant access and select next as well.
In the Authentication Methods clear the following check-boxes and select the Unencrypted Authentication (PAP, SPAP), select next and disregard the warning. On the following screen Configure Constraints accept the defaults select next.
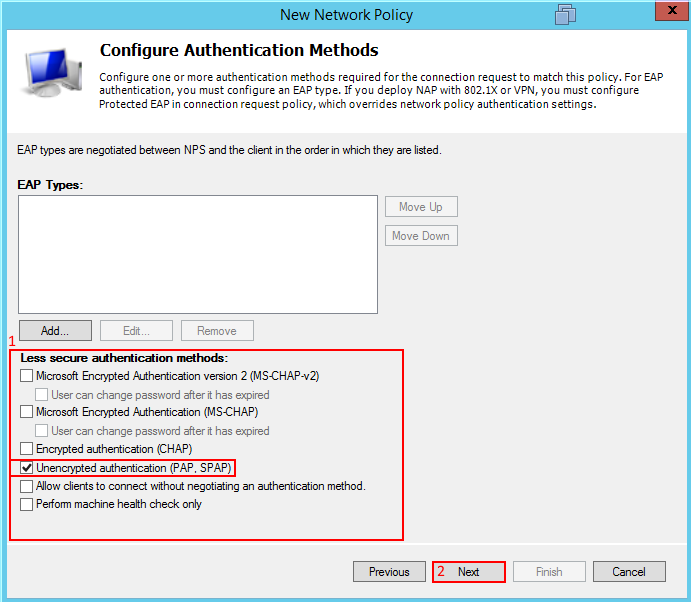
We should be at the Configure Settings page, under the Radius Attributes delete the existing attributes and add Service-Type Administrative.
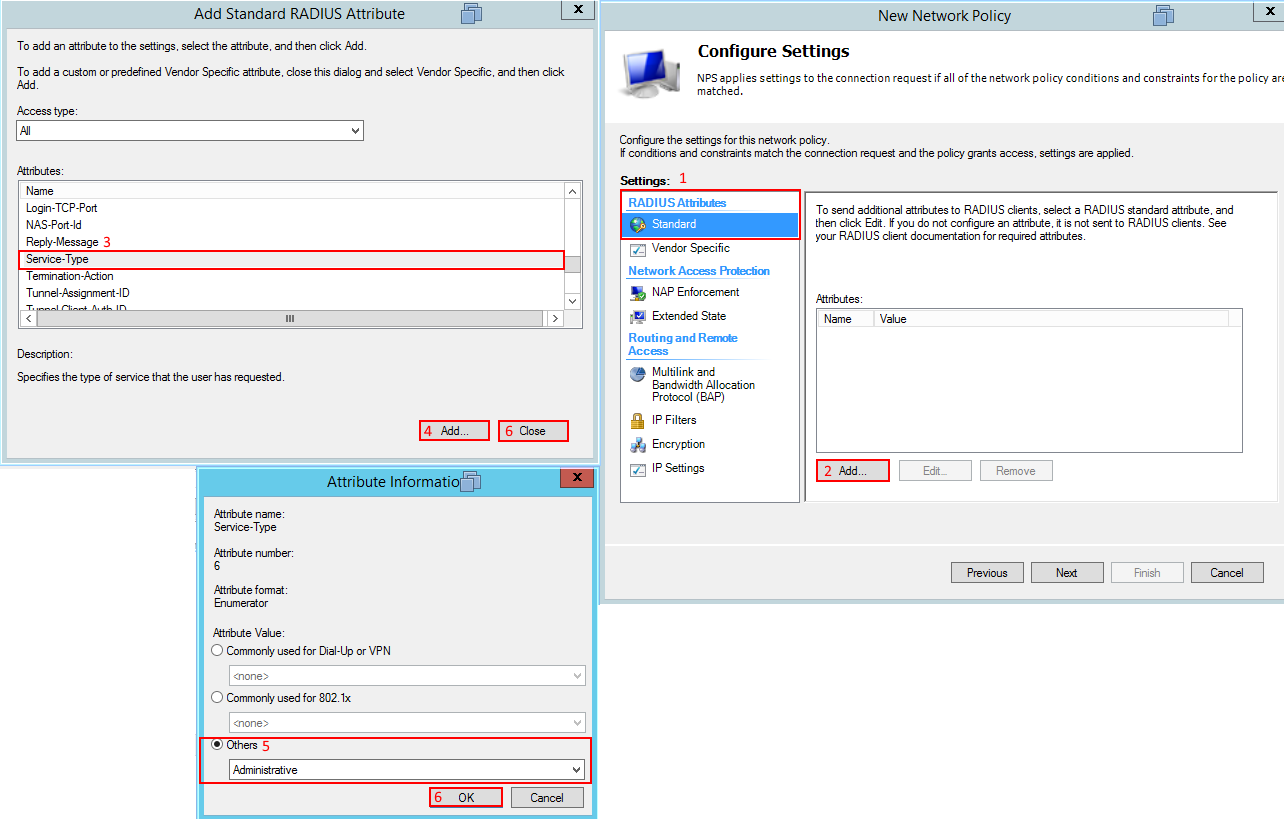
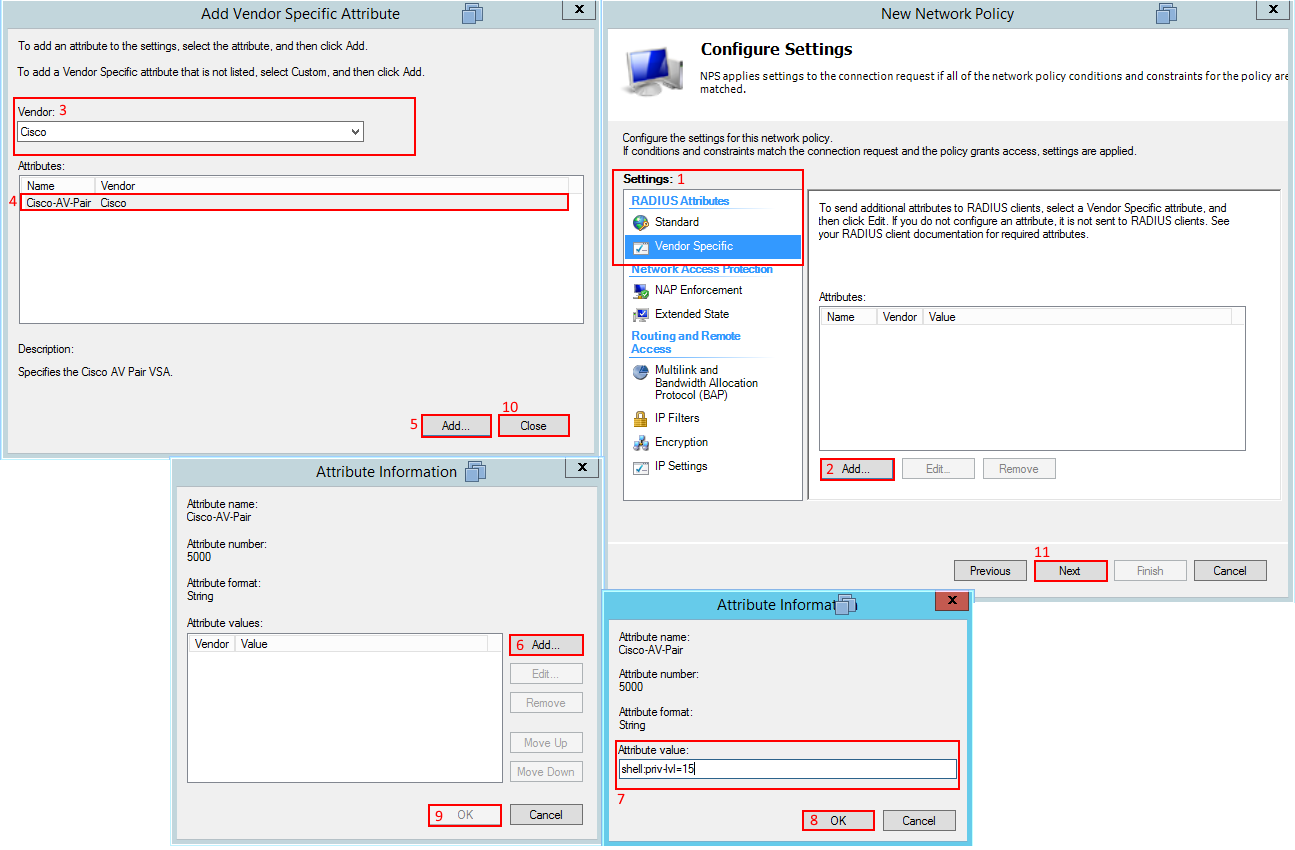
Under Vendor Specific we need to add to a Cisco-AV Pair to tell the router to go to privilege level 15, select next when you add the shell:priv-lvl=15 in the Cisco-AV.
1login as: ryan
2
3**************************************************************************
4* IOSv is strictly limited to use for evaluation, demonstration and IOS *
5* education. IOSv is provided as-is and is not supported by Cisco's *
6* Technical Advisory Center. Any use or disclosure, in whole or in part, *
7* of the IOSv Software or Documentation to any third party for any *
8* purposes is expressly prohibited except as otherwise authorized by *
9* Cisco in writing. *
10**************************************************************************
11Using keyboard-interactive authentication.
12Password:
13
14**************************************************************************
15* IOSv is strictly limited to use for evaluation, demonstration and IOS *
16* education. IOSv is provided as-is and is not supported by Cisco's *
17* Technical Advisory Center. Any use or disclosure, in whole or in part, *
18* of the IOSv Software or Documentation to any third party for any *
19* purposes is expressly prohibited except as otherwise authorized by *
20* Cisco in writing. *
21**************************************************************************
22HQ#
23HQ#show privilege
24Current privilege level is 15
25HQ#
Here is the debug information of AAA when I logged into the router using radius:
1HQ#debug aaa authentication
2AAA Authentication debugging is on
3HQ#debug aaa authorization
4AAA Authorization debugging is on
5HQ#
6*Mar 13 18:36:59.854: AAA/BIND(00000013): Bind i/f
7*Mar 13 18:36:59.855: AAA/AUTHEN/LOGIN (00000013): Pick method list 'RADIUS-LOCAL'
8*Mar 13 18:37:03.553: AAA/AUTHOR/EXEC(00000013): processing AV priv-lvl=15
9*Mar 13 18:37:03.553: AAA/AUTHOR/EXEC(00000013): processing AV priv-lvl=15
10*Mar 13 18:37:03.554: AAA/AUTHOR/EXEC(00000013): processing AV service-type=6
11*Mar 13 18:37:03.554: AAA/AUTHOR/EXEC(00000013): Authorization successful
So we have done pretty good but what about if we had a junior network technician and we did not want to allow full administration access to the device but this technician needs to be able to use show commands? How would we be able to do this with radius? Well with Cisco IOS you can use parser views, basically you configure a parser view on the IOS router call it name and configure the view to only allow the commands you want. You configure the radius server to pass the name of the parser view you created on the IOS router, if the parser view name matches the router will put that user into that view and only allow the user to use the commands that are configured in that view. More information about parser views can be found on Cisco website: Role-Based CLI Access
So in this example we are going to create a parser view called SHOWMODE and only allow show commands. In the enable prompt we want to be in "root view mode" to do this we would type enable view, the router is going to be asking for a password and that is your enable secret password you created at the beginning of this post.
NOTE: If you have Radius enabled you will have to at least disable the client in NPS when you are first configuring a parser view. By disabling the client in NPS the router will fail-back to its local database of username and passwords to authenticate. The reason for this is because the router will try to use the NPS server to authenticate, this may not sound like a problem but the router is not using your username when you issue the command enable view. If your radius server has logging enabled you'll see that the router is using a different username called root. Since root is not in our Windows Active Directory the radius server will reject the request. Although you could create a user called root in Windows Active directory and put that user in the correct security groups to allow logins using radius that just doesn't sound like a good idea. The simplest method is to disable the client in NPS and use your enable secret password. Give it a second or two as this has to timeout before it fails-back to the local username and password database.
1login as: ryan
2
3**************************************************************************
4* IOSv is strictly limited to use for evaluation, demonstration and IOS *
5* education. IOSv is provided as-is and is not supported by Cisco's *
6* Technical Advisory Center. Any use or disclosure, in whole or in part, *
7* of the IOSv Software or Documentation to any third party for any *
8* purposes is expressly prohibited except as otherwise authorized by *
9* Cisco in writing. *
10**************************************************************************
11Using keyboard-interactive authentication.
12Password:
13
14**************************************************************************
15* IOSv is strictly limited to use for evaluation, demonstration and IOS *
16* education. IOSv is provided as-is and is not supported by Cisco's *
17* Technical Advisory Center. Any use or disclosure, in whole or in part, *
18* of the IOSv Software or Documentation to any third party for any *
19* purposes is expressly prohibited except as otherwise authorized by *
20* Cisco in writing. *
21**************************************************************************
22HQ#
23!
24!DISABLE: the client in NPS before you type the command enable view
25!
26HQ#
27HQ#enable view
28Password:
29
30HQ#show privilege
31Currently in View Context with view 'root'
32HQ#
Now that we have verified we are in "root view" let's go to configuration mode and create a parser view called SHOWMODE. We also have to create another secret password this should be different from the enable secret.
1HQ(config)#parser view SHOWMODE
2HQ(config-view)#secret 0 cisco123
Once we have the password created we can tell the router what commands we want to allow in this view. In this example we are only allowing show commands so the command would be:
1HQ(config-view)#commands exec include all show
2HQ(config-view)#exit
3HQ(config)#exit
We can test this parser view by going into it by using the command enable view SHOWMODE. We are prompt for the password to enter this view (Again the client on NPS should be disabled so that we can use our local username and password database on the router).
1HQ#enable view SHOWMODE
2Password:
3
4HQ#show privilege
5Currently in View Context with view 'SHOWMODE'
6HQ#
If I issue a question mark (?) I get a list of the commands I can issue: (It looks I can only use show commands)
1HQ#?
2Exec commands:
3 <1-99> Session number to resume
4 do-exec Mode-independent "do-exec" prefix support
5 enable Turn on privileged commands
6 exit Exit from the EXEC
7 show Show running system information
8
9HQ#
So we have created a parser view on our router now lets configure our Microsoft NPS server to use that parser view when our junior technician logs into this router. We have to create a new network policy in NPS. In this example I'm calling it Allow Network Operators - Read Only. Follow the steps you did before when we first created the Network Administrators policy the only difference of course is going to be a different Windows Active Directory security group and our radius attributes. We only need to focus on the Vendor Specific section of the network policy under the radius attributes section. We need to add a different Cisco AV-Pair called shell:cli-view-name=SHOWMODE and also add the shell:priv-lvl=15.
It would look something like this, select next.
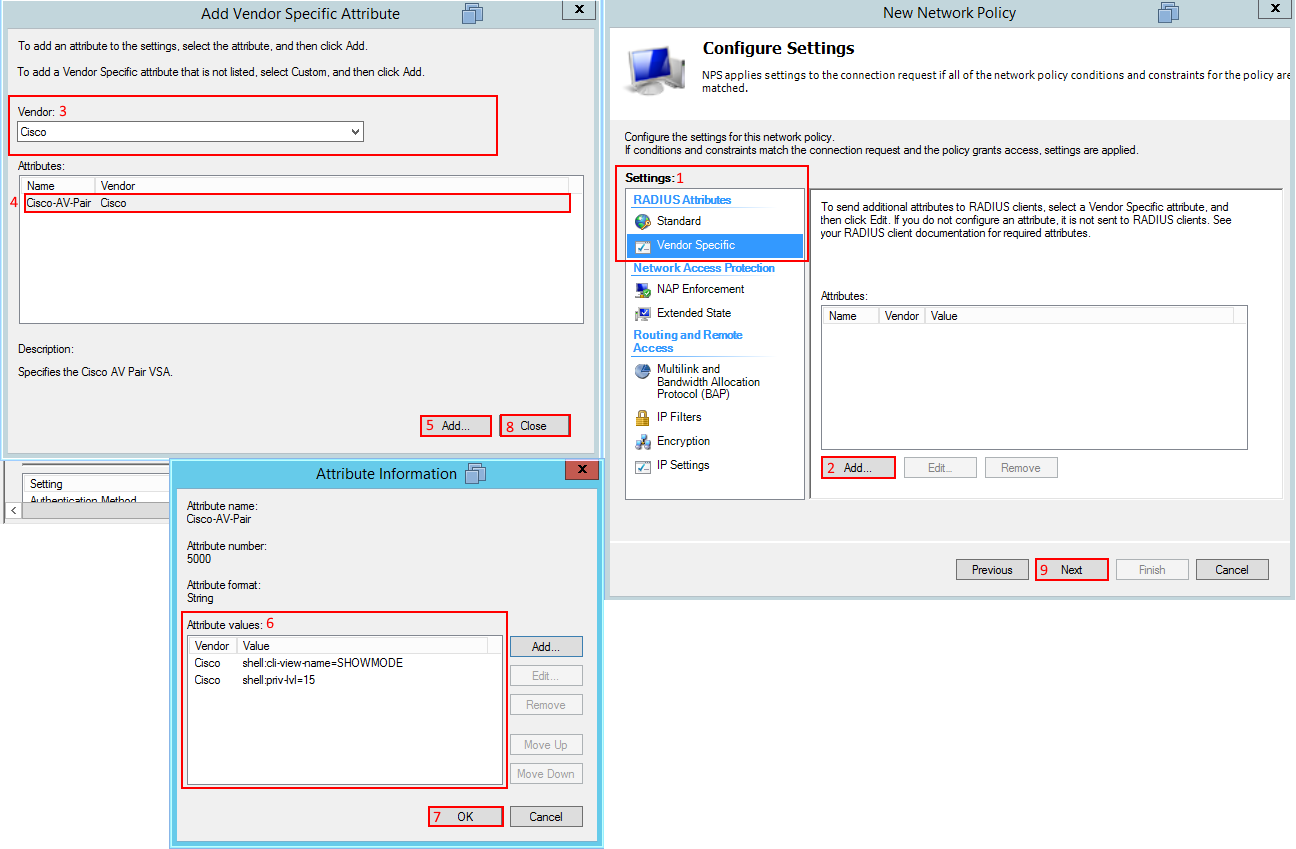
We now should be at the summary screen of the new policy we just created and to give you a reference here is what I have for this example.
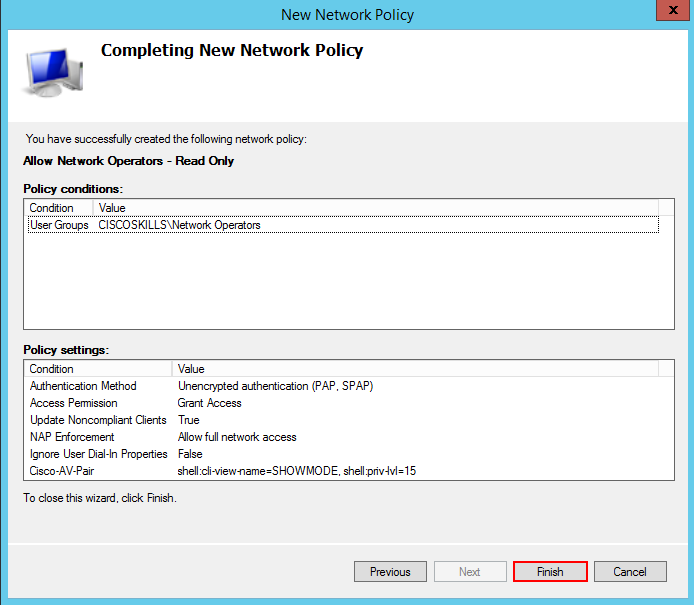
Once we select finish we should be able to login to our router but this time it is going to be using the parser view we created. Joe is another account I have created in Windows Active Directory and this account is part of the network operators security group. Here is what I have when Joe logs into the router.
1login as: joe
2
3**************************************************************************
4* IOSv is strictly limited to use for evaluation, demonstration and IOS *
5* education. IOSv is provided as-is and is not supported by Cisco's *
6* Technical Advisory Center. Any use or disclosure, in whole or in part, *
7* of the IOSv Software or Documentation to any third party for any *
8* purposes is expressly prohibited except as otherwise authorized by *
9* Cisco in writing. *
10**************************************************************************
11Using keyboard-interactive authentication.
12Password:
13
14**************************************************************************
15* IOSv is strictly limited to use for evaluation, demonstration and IOS *
16* education. IOSv is provided as-is and is not supported by Cisco's *
17* Technical Advisory Center. Any use or disclosure, in whole or in part, *
18* of the IOSv Software or Documentation to any third party for any *
19* purposes is expressly prohibited except as otherwise authorized by *
20* Cisco in writing. *
21**************************************************************************
22HQ#
23HQ#
24HQ#show privilege
25Currently in View Context with view 'SHOWMODE'
26HQ#
27HQ#?
28Exec commands:
29 <1-99> Session number to resume
30 do-exec Mode-independent "do-exec" prefix support
31 enable Turn on privileged commands
32 exit Exit from the EXEC
33 show Show running system information
34
35HQ#
As we can see Joe can only issue show commands and we can verify what privilege Joe is under by issuing the show privilege command notice Joe is using the SHOWMODE parser view we created on the IOS router, how cool cat is that ;)
Believe it or not that's it for this post. We have created policies on Microsoft NPS server as well as created parser views to limit access based on user accounts and tied it all together using radius. I hope this this information is helpful in helping you build a better RBAC with your network devices!
Static Comments:
Ryan -
Hey Darkpenguin, Privilege levels are hierarchical where as parser views are role based, so they are two different things. I can specifically call out different commands to use under a parser view regardless if its at a lower or higher privilege level. If you look at the example where the username Joe logs into the router, although this account has privilege level 15 this account is tied to a parser view called SHOWMODE. This account could only do show commands regardless what the privilege level was set. I really don't need to worry about privilege levels if I'm using parser views, however you could give them a lower privilege level but I think the end result would be the same, they would only be able to use show commands on that lower privilege level. So I'm not sure what benefit you would get from putting this group at a lower privilege level. Ryan
Why add the "shell:priv-lvl=15" to the view only group?