Understanding CBAC
Although using hardware firewalls are an excellent step forward when securing your network. They can cost money and are not cheap to set up and configure. Using CBAC is built-into the Cisco IOS router and helps filter those unwanted protocols that are in your network. When setting up routers as firewalls you have some choices like using CBAC the "Classic" firewall, or zone based policy (ZBF). Today we will talk about CBAC and how to understand the core components of what make CBAC possible. CBAC stands for Content-Base-Access-Control and uses ACLs. (Access Control Lists) Unlike the established TCP session and reflexive ACLs CBAC has several advantages:
- Monitors TCP connections, (Three-way handshake)
- Maintains UDP session information
- Tracks TCP sequence numbers
- Inspects DNS queries and replies
- Inspect common ICMP messages types
- Supports applications that rely on multiple connections (FTP)
- Inspects embedded address
- Inspects Application Layer information
ACLs only look at the network layer and sometimes the transport layer. CBAC is application aware, meaning CBAC is a stateful firewall which keeps track of the state of network connections such as TCP streams, and UDP communication travelling across it. The firewall is programmed to distinguish legitimate packets for different types of connections. Only packets matching a known connection state will be allowed by the firewall; others will be rejected. Because CBAC only matches packets (TCP, UDP and other protocols) it was specified to look at, it will then depend on the ACL if that packet is allowed access or denied. CBAC creates openings in ACLs at the interfaces that inspect the traffic by adding a temporary ACL entry for a specific session. The openings are created when the internal network starts a session with the outside network that would normally be denied. The traffic is only allowed back through the firewall if it is part of the same session and has the correct properties that CBAC is looking for. For example let's say a user starts an http session in the protected network and the packet moves to the outside or unprotected network. CBAC is configured to inspect http traffic and there is an ACL on the inbound (outside interface) blocking http traffic from the unprotected network to the protected network. So the packet is allowed access to the unprotected network because the ACL is on the inbound interface and not the outbound interface. So the ACL does not look at the packet, CBAC however looks at the packet and in the inspection rules the packet is allowed access to the unprotected network, CBAC adds an entry in its state table. Because a new entry is added a dynamic ACL is created on the external interface to the protected network. This dynamic ACL will allow http traffic back into the protected network. This opening is only active it the session is open, once the session closes the ACL is removed. Once removed any traffic that starts from the unprotected network will be denied access to the protected network. This depends on the ACL which checks inbound connections from the unprotected network.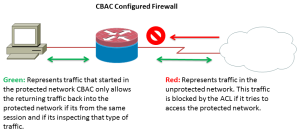
- Pick an interface of where you want CBAC to be inspecting; this depends on the flow of your network and the amount of interfaces you have installed on your router. (DMZ, Web server, E-mail servers, etc.)
- Configure IP ACLs at the interface. The network technician must define what type of traffic is allowed and will not be inspected by CBAC and which traffic is blocked and will be inspected by CBAC.
- Define inspection rules. The network technician should specify each desired application layer to inspect along with generic TCP, ICMP and or UDP fields. Inspection rules are configured by statements each listing a protocol and specifying the inspection rule name.
- Finally apply the inspection rule to an interface.
CBAC is considered the "classic" firewall compared to zone based, it is relatively simple to configure and understand. However unlike zone based CBAC can get complex when multiple CBAC configurations on a router exists. Remember CBAC also uses ACLs if configured and implemented poorly these ACLs can block traffic even when CBAC allows them. I hope this tutorial was helpful.