TACACS Plus and RADIUS
TACACS+ and RADIUS are both used to control access to network resources, but both of these protocols are different in how they operate depending how you want to secure your network. These protocols need to have (AAA) authentication, authorization, and accounting setup on the routers before you can set up these access server protocols. First let's get some information on why we would need this type of access server protocol setup. Usually you will find this setup in medium to enterprise environments. What the access server does is provide a central location of all the users and privileges these users can do on network resources. If we did not have a server we would have to put these users manually on the Cisco IOS software and that could be time-consuming depending on how many devices (routers, switches) there are in your network infrastructure. So what can RADIUS and TACACS+ do? Both can provide a central location on who can access the network resources but both are different in how they authorize users. RADIUS is an access sever that uses the AAA and uses the UDP protocol. For Network security the information that is sent between the client and the server is authenticated by a shared password which is never sent over the network. Also any user passwords are encrypted between the client and the server. However one thing that is different between TACACS+ and RADIUS is with TACACS+ the whole packet is encrypted, RADIUS only encrypts the password everything else is in plain text for example the user name. RADIUS is able to support a variety of methods to authenticate a user when a username and password are sent. RADIUS can support PPP, PAP, CHAP, UNIX login and other authentication mechanisms. Over TACACS+ RADIUS is also available for free at various websites. Finally RADIUS combines authentication and authorization meaning once the user has been granted access the RAIDUS server is done and no longer is involved. RADIUS sends the privileges to the network device and it is up to the device to be able to allow or disallow certain commands and functions. 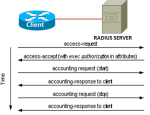
- TCP usages provide a separate acknowledgment that a request has been received, regardless of how loaded and slow the backend authentication mechanism.
- TCP provides immediate indication of a crashed, or not running, server by a reset (RST). You can determine when a server crashes and returns to service if you use long−lived TCP connections. UDP cannot tell the difference between a server that is down, a slow server, and a non−existent server.
- Using TCP keepalives, server crashes can be detected out−of−band with actual requests. Connections to multiple servers can be maintained simultaneously, and you only need to send messages to the ones that are known to be up and running.
- TCP is also more scalable and adapts to growing, as well as congested, networks.
Like mentioned above TACACS+ encrypts the entire packet, besides the standard header, RADIUS only encrypts the password. TACACS+ uses the AAA protocol like RADIUS but during a session the client checks with TACACS+ server to determine if the user is granted permission to use different commands and or functions. By doing this it provides greater control over commands that can be executed on the network resources. 